Introduction
"Network Security Group doesn't have supporting Security Rule for Network Intent Policy Security Rule"If you’re trying to deploy Azure SQL Managed Instance in Azure via Azure Bicep you may have stumbled across this ‘Network Intent Policy’ error when trying to redeploy your Azure Bicep template.
The problem doesn’t present itself on your first deployment yet when trying your template again this error is present. It seems if we don’t define the network security group rules and routes for the SQL Managed Instance network intent explicitly in our Bicep template then ARM believes something is either changing or being redeployed. To me, this goes against the idempotent nature of ARM/Bicep to a degree.
At the time, I was referencing the CARML modules for Azure SQL Managed Instance for what I should include in my template, which did have some rules defined around network intent policy rules. However, these were not working for me. I later discovered the rules defined were the pre November 2022 mandatory rules and so not valid for my deployment.
In my searches I could not find any off the shelf Bicep code for the current rules, so I decided to put something together in hope it helps others get around the error quicker than I did.
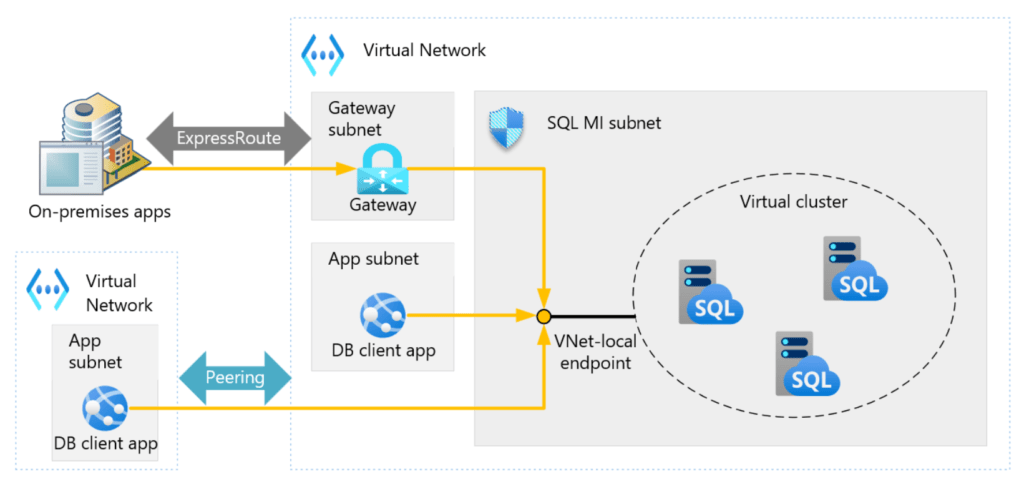
What is the network intent policy?
In order for Azure SQL Managed Instance to function correctly, it needs certain rules and routes defined and those rules must remain in place. Microsoft state:
“To improve service security, manageability, and availability, SQL Managed Instance applies a network intent policy on some elements of the Azure virtual network infrastructure. The policy configures the subnet, the associated network security group, and the route table to ensure that the minimum requirements for SQL Managed Instance are met. “
Connectivity architecture – Azure SQL Managed Instance | Microsoft Learn
The fix to make your Azure Bicep templates idempotent
In order to fix the network intent policy error and have a Bicep template that can be redeployed over and over again we must define the network intent policy rules in the Bicep template after initial deployment.
Here is the current NSG security rules & route table routes for Azure SQL Managed Instance with Bicep that I’ve put together. Built from the following Azure SQL Managed Instance connectivity table here.
https://gist.github.com/riosengineer/3cbb4bf725030d0ee54f3944a35427d8
These networking objects have been created based on what the current architecture requires for the security rules & routes, which sets out the mandatory rules and routes required for Azure SQL Managed Instance to work properly.
I also stumbled across others having a similar problem with ARM/Bicep in Azure Databricks which would require the same solution by defining the necessary rules and routes Can’t redeploy Network Security Group for Databricks VNet injection · Issue #6670 · Azure/azure-quickstart-templates · GitHub.
Alternatively, after the initial Azure SQL Managed Instance deployment, go to your Network Security Group and Route table, export to template and convert to Bicep using the decompile command (or if you have the VSCode extension, it should auto-convert on paste!): az bicep decompile --file main.json
What’s your thoughts?
Hopefully this saves others some time when trying to create their Azure Bicep SQL Managed Instance templates! There is a GitHub issue open which seems like others are hitting the same hurdle too:
Resource types for Network Intent Policies · Issue #1755 · Azure/bicep-types-az · GitHub
Hopefully this helps someone else out there who comes across this issue. Let me know in the comments if you had a similar problem.