Introduction 🤖
In this blog, I’ll detail how you can integrate GitHub Dependabot with Azure DevOps at no cost, ensuring you can proactively monitor vulnerabilities in your project dependencies and keep them up-to-date in your .NET projects!
For those unaware, Dependabot is a bot designed to help developers keep their software dependencies up-to-date by scanning the project for outdated dependencies, usually on a set schedule via an automated pipeline. This is especially useful for proactively addressing security vulnerabilities within your .NET projects. What’s not to like about that?
Dependabot has made the core library open source so that those organisations and individuals not invested into the GitHub ecosystem can still leverage the bot, and that is exactly what the awesome team at Tingle Software have done with the project for Azure DevOps users.
Whilst this blog covers Azure DevOps .NET projects via a private artifact feed, dependabot supports various feeds (and other languages) for your own workflows, check them out here.
Setup
Extension install
Firstly, you’ll need to go ahead and install the Dependabot for Azure DevOps extension via the marketplace so that the task is available to call:
In Azure DevOps, go to your ‘Organization Settings > Extensions’ area and ‘Browse marketplace’ to search for and install the Azure DevOps extension:
YAML
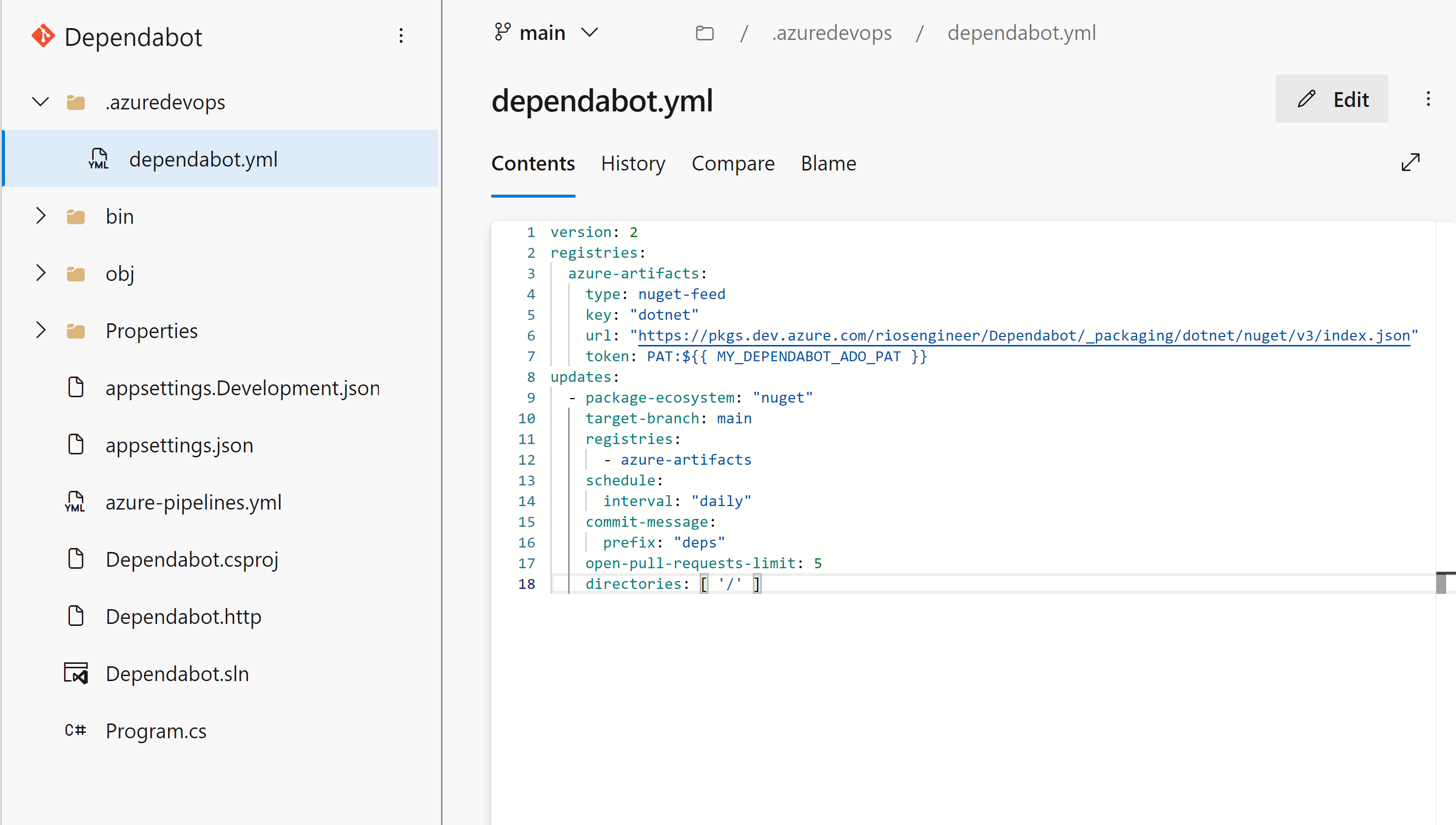
Dependabot configuration
Next, you’ll want to configure the .azuredevops/dependabot.yml configuration file. The file path must be within the .azuredevops or .github folder in your root repository. Below is a quickstart example for a .NET NuGet feed via Azure Artifacts, but you can configure the file to your needs using the documentation here.
Azure Pipeline
Next, you’ll need to set up an Azure Pipeline to run the Dependabot scan on your desired schedule. In my example, it’s set to run weekly, but you can also manually run the pipeline on your branch whenever you want to test immediately. Create your desired pipeline file, e.g., azure-pipelines.yml, and add the YAML configuration below as a starting point. The dependabot@2 task has many settings that can be customised, see here.
Create your Azure Pipelines from the existing yaml file: Pipelines > New pipeline > Azure Repos Git > Repo > Existing YAML file.
Azure DevOps Permissions
Now, you’ll need to grant the Azure DevOps Build Service user access to create a branch, push, and contribute to a pull request so the bot task can scan, create a temporary branch with the changes, and finally create the pull request for review. To do this, go to ‘Project Settings’ > Repositories > YOUR REPO > Security > Users/Build Service:
Grant:
- Contribute: Allow
- Contribute to pull requests: Allow
- Create branch: Allow
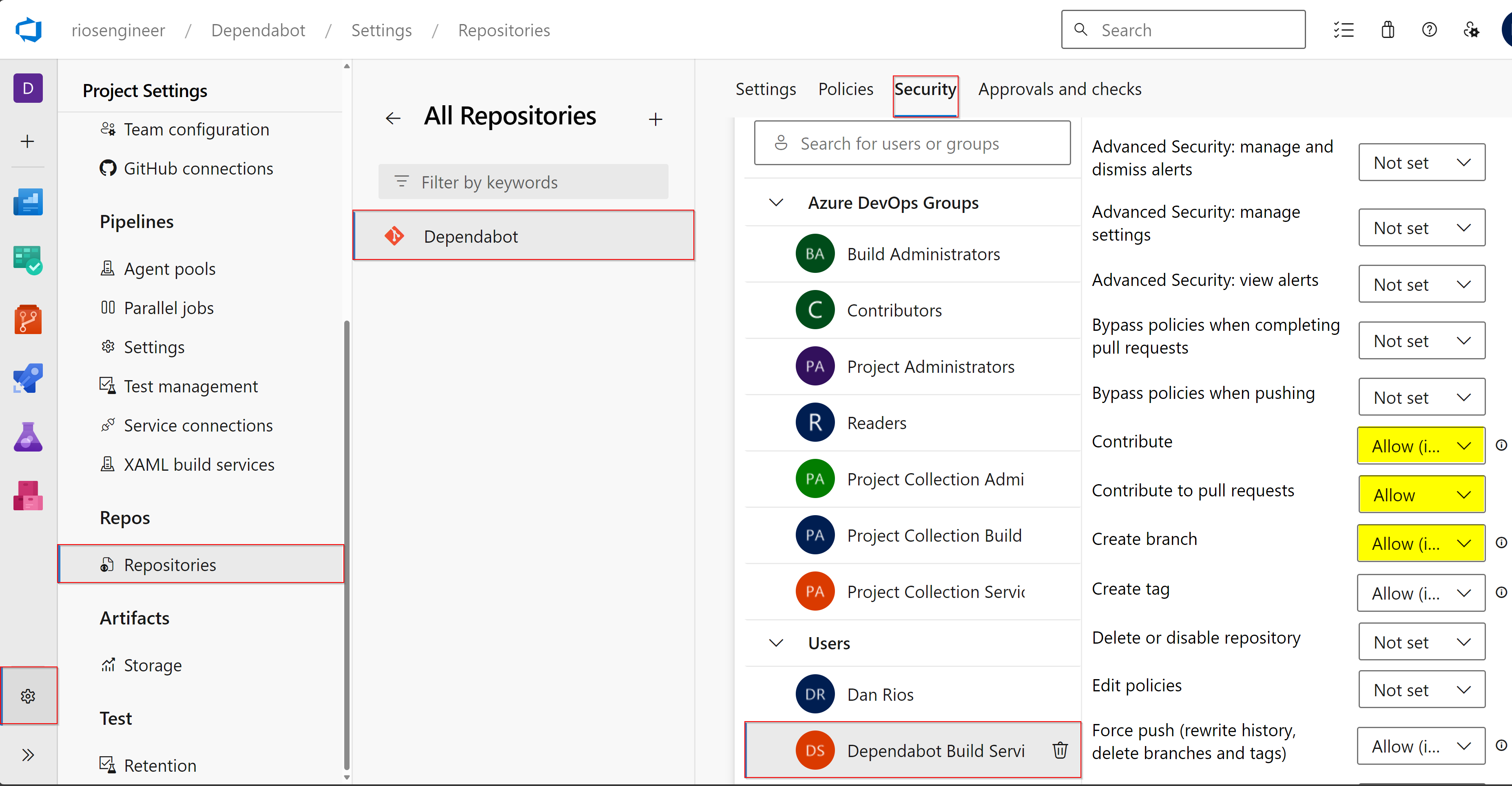
This is what the token: $(System.AccessToken) is using when the Pipeline runs (as it runs under the build service account) within the Azure Pipeline.
PAT
Finally, you need to add a PAT for private Azure Artifact feed access so Dependabot can successfully check the dependencies. You’ll need a PAT with Packaging (read) access scope so Dependabot can scan the dependencies in your private artifacts feed that your project uses.
Click the profile settings icon at the top right (next to your profile circle) and select Personal access tokens (show more scopes):
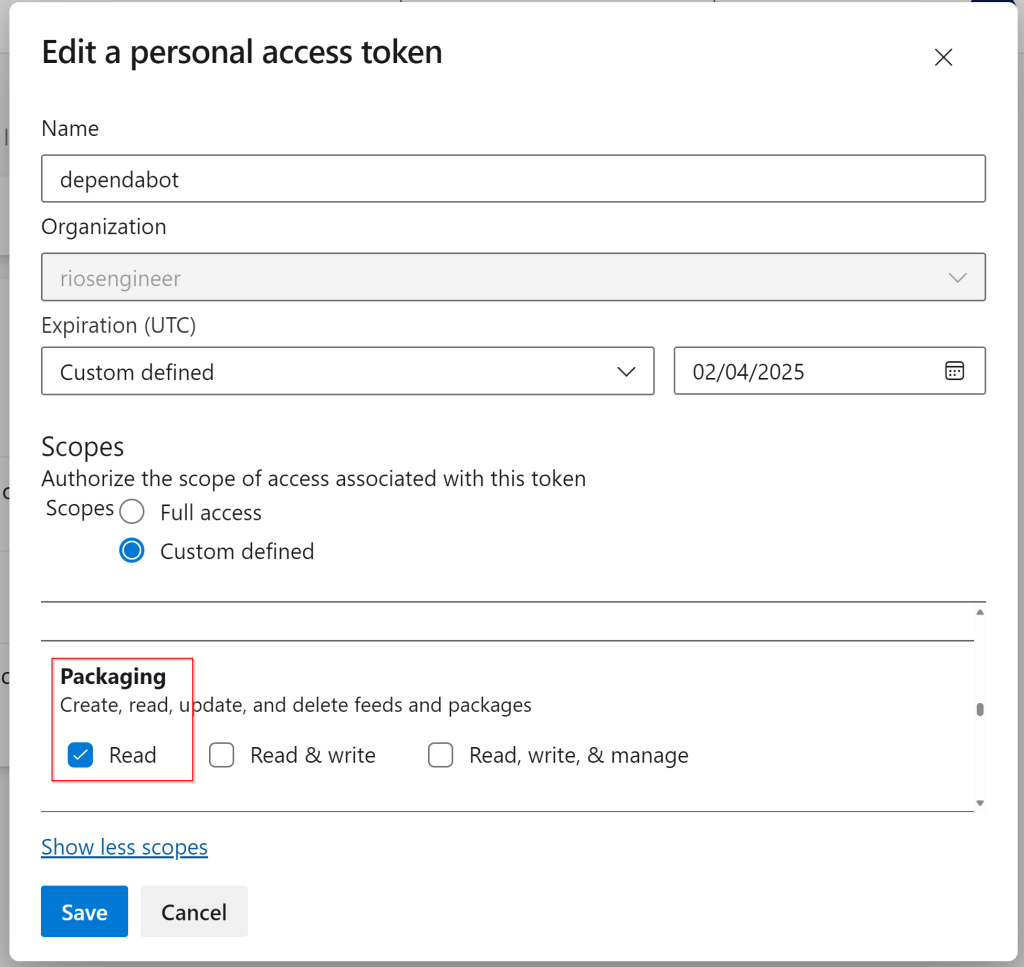
Lastly, add this PAT value to your Azure DevOps library, which you will reference in the azure-pipelines.yml file as a variable group. This will expose the PAT token as an environment variable, granting access when the bot runs.
In action 🚀
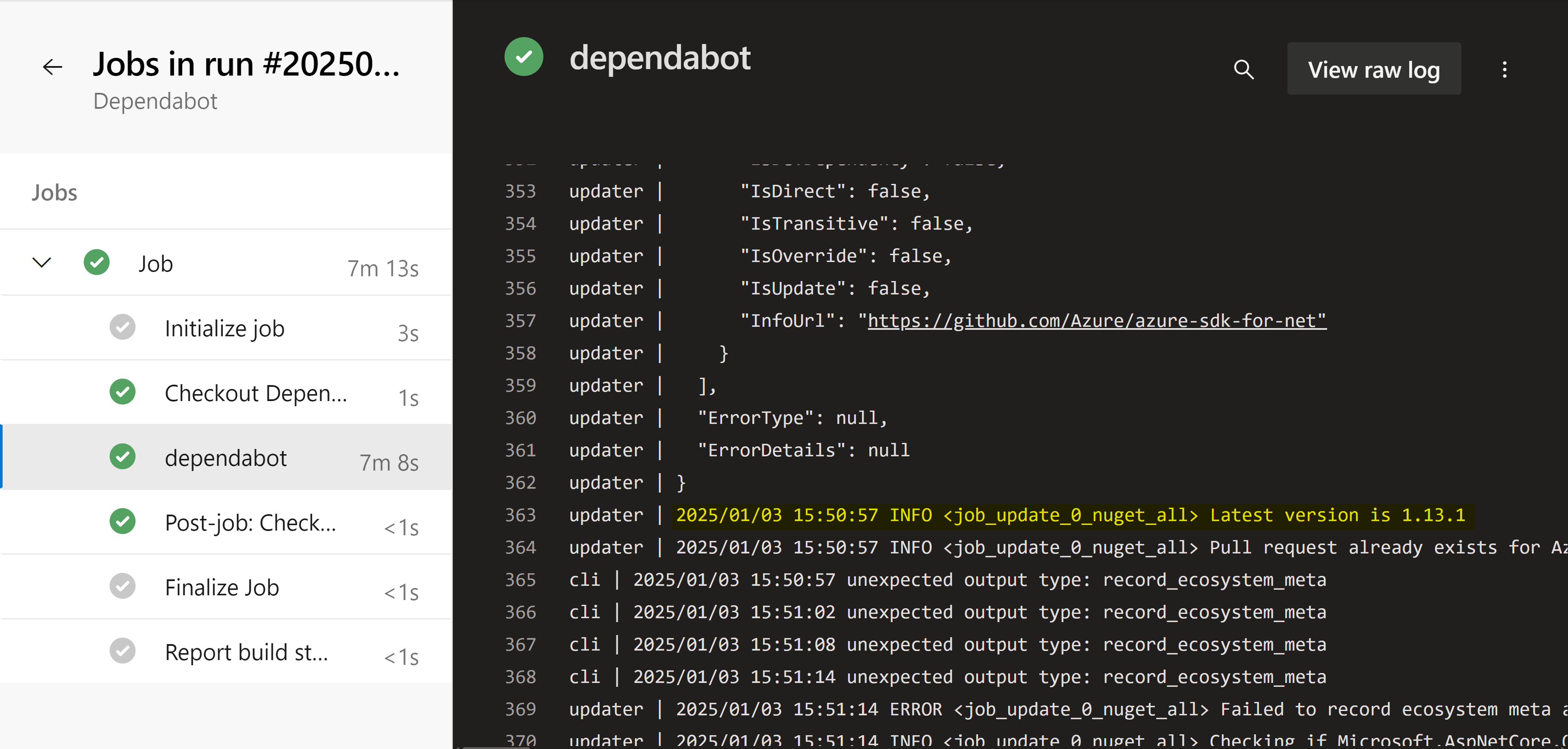
Lastly, manually run the pipeline and wait for it to complete to review the scan output and pull request action. In my example, I’m deliberately using an older Azure.Identity package version that I know has vulnerabilities. My project is pulling from a private Azure Artifact feed, with the upstream feed being the public NuGet source.
When running the pipeline manually, it picks up the latest Azure.Identity version, which at the time of writing is 1.13.1.
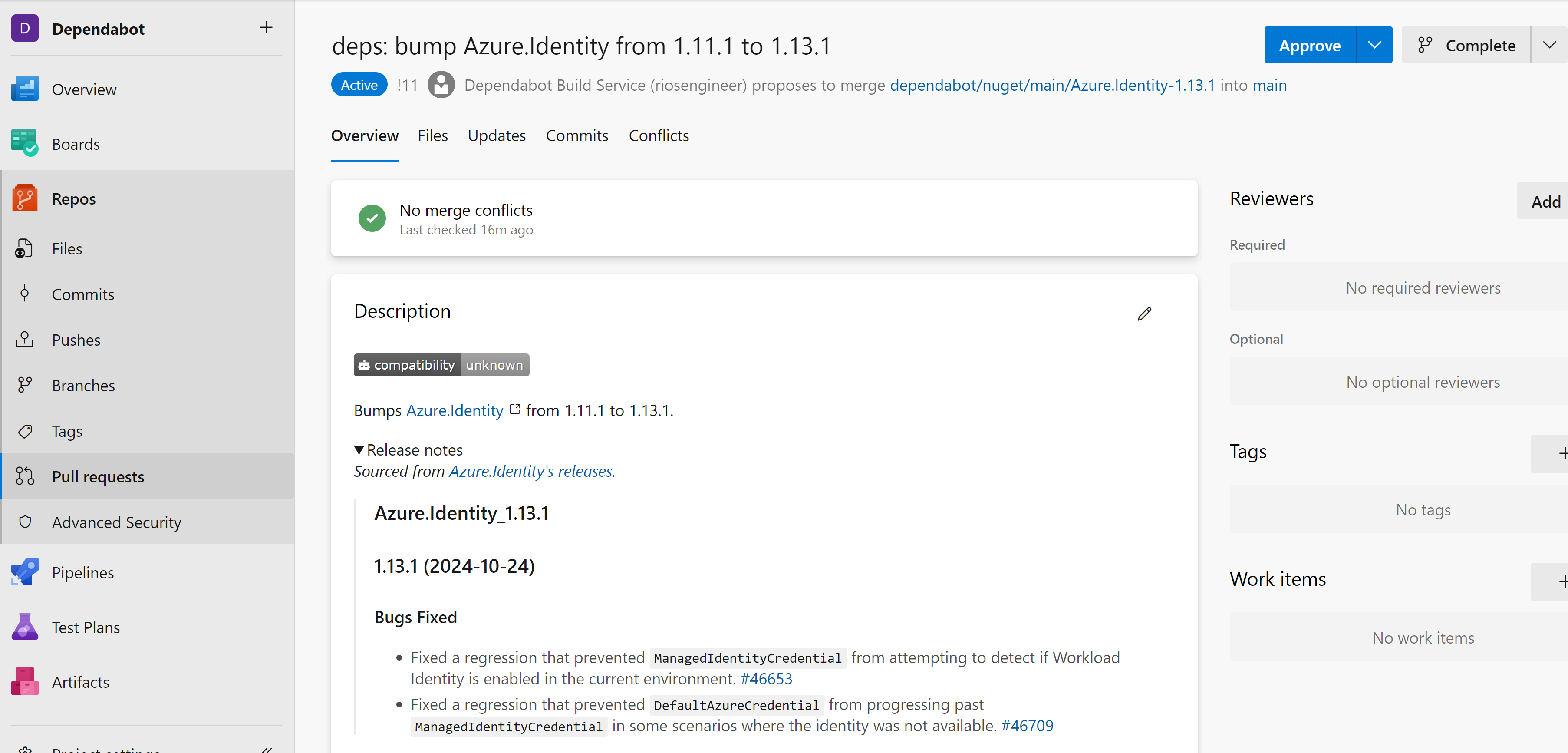
Now that the pipeline with the bot scan has completed, you’ll notice an active pull request waiting for review. It details the dependency found, the version it will be updated to, and includes release notes about the update:
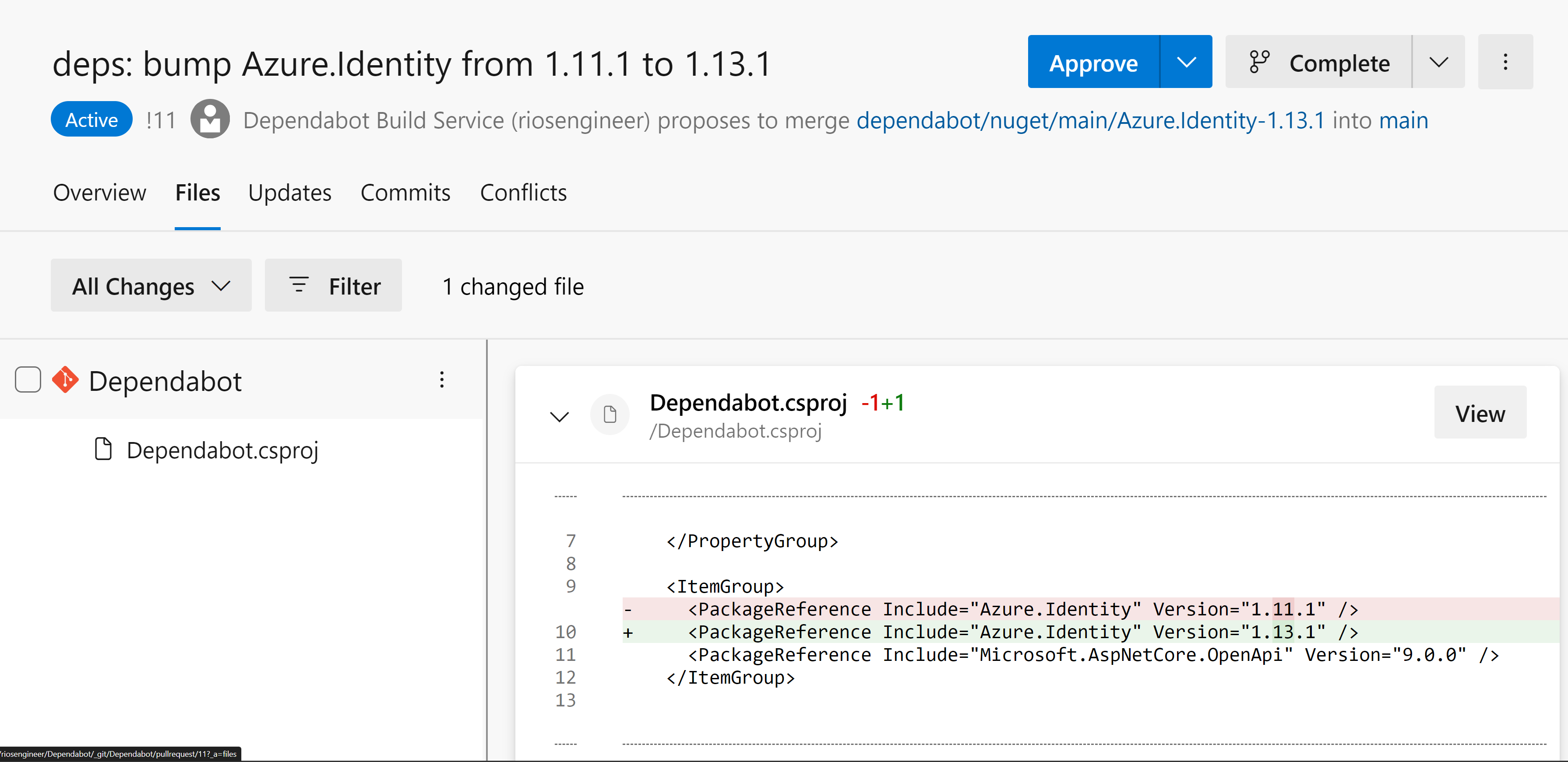
Lastly, we see the bot has modified the .csproj file to update the package reference version to the latest version 🎉
Conclusion
That’s it. It’s pretty awesome and a great proactive tool to add to your workflow, ensuring your project dependencies don’t expose you to security vulnerabilities and other issues. The bot can be heavily customised and supports many languages (e.g., Python, Java, etc.), not just .NET. It uses various feeds for updates, all of which can be reviewed in the official Dependabot documentation. You can then tweak or add further configurations in the dependabot.yml file.
Let me know your thoughts, if you’re using it, did you even know it was available to integrate to Azure DevOps?
hi dan,
I’m getting the following error following this example, any ideas?
updater | 2025/04/03 11:18:21 INFO Discovery JSON path for workspace path [/] found in file [/home/dependabot/.dependabot/discovery_map.json] at location [/home/dependabot/.dependabot/discovery.1.json]
updater | 2025/04/03 11:18:21 INFO Discovery JSON path for workspace path [/] found in file [/home/dependabot/.dependabot/discovery_map.json] at location [/home/dependabot/.dependabot/discovery.1.json]
updater | 2025/04/03 11:18:21 ERROR Error during file fetching; aborting: No files found in /
{“data”:{“error-type”:”dependency_file_not_found”,”error-details”:{“file-path”:null,”message”:”No files found in /”}},”type”:”record_update_job_error”}
{“data”:{“base-commit-sha”:”7539356ce08520ee1c3677a9a29f1435fbb931aa”},”type”:”mark_as_processed”}
If this because I am missing a config file?
I have a file called dependabot.yml as per the instructions and another yaml file to run the pipeline / task: dependabot@2
Although looking at logs I also have this error, so maybe an auth error that is mentioned elsewhere?
cli | 2025/04/03 13:52:11 Failed to find credentials for GitHub container registry.
cli | 2025/04/03 13:52:11 pulling image: ghcr.io/github/dependabot-update-job-proxy/dependabot-update-job-proxy:latest
cli | 2025/04/03 13:52:14 using image ghcr.io/github/dependabot-update-job-proxy/dependabot-update-job-proxy:latest
Hi Mark!
That GitHub registry pulling error is present in all my pipelines, can assume it’s safe to ignore and not related to your issue.
Do you have a dependabot.yml file in your repository somewhere? then there will be a directories: [ ‘/‘ ] property in that config yml, is it possible this isn’t set? It looks like it just can’t find a directory to scan. It’s almost working 🚀