Introduction
A quick blog to demonstrate a solution for enforcing that Log Analytic Workspaces in your environment are created with a daily quota property value set. This can be useful if you want to guardrail against workspaces created without this value set, which can in some instances can help stop incurring large ingestion costs unexpectedly. This is going to be most useful for organisations that are using a decentralised analytics model over a single workspace or for legacy tenants where a typical landing zone implementation is yet to be implemented.
Policy Definition
Below is the Azure Policy definition (custom) that will deny creation of Azure Log Analytics Workspaces that do not have a value defined in the daily quota property for use:
{
"properties": {
"displayName": "Deny creation of Log Analytics workspace without daily quota",
"policyType": "Custom",
"mode": "All",
"description": "This policy denies the creation of Log Analytics workspaces if the daily quota is not set.",
"metadata": {
"version": "1.0.0",
"category": "Log Analytics"
},
"parameters": {
"effect": {
"type": "string",
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the policy"
},
"allowedValues": [
"Audit",
"AuditIfNotExists",
"Deny"
],
"defaultValue": "Deny"
}
},
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.OperationalInsights/workspaces"
},
{
"field": "Microsoft.OperationalInsights/workspaces/workspaceCapping.dailyQuotaGb",
"exists": false
}
]
},
"then": {
"effect": "[parameters('effect')]"
}
}
}
}EPAC Definition
If your organisation is leveraging EPAC (Enterprise Policy as Code) then this is a EPAC friendly definition to use:
{
"$schema": "https://raw.githubusercontent.com/Azure/enterprise-azure-policy-as-code/main/Schemas/policy-definition-schema.json",
"name": "Deny-LAW-Without-Quota",
"properties": {
"displayName": "Deny creation of Log Analytics workspace without daily quota",
"policyType": "Custom",
"mode": "All",
"description": "This policy denies the creation of Log Analytics workspaces if the daily quota is not set.",
"metadata": {
"version": "1.0.0",
"category": "Log Analytics"
},
"parameters": {
"effect": {
"type": "string",
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the policy"
},
"allowedValues": [
"Audit",
"AuditIfNotExists",
"Deny"
],
"defaultValue": "Deny"
}
},
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.OperationalInsights/workspaces"
},
{
"field": "Microsoft.OperationalInsights/workspaces/workspaceCapping.dailyQuotaGb",
"exists": false
}
]
},
"then": {
"effect": "[parameters('effect')]"
}
}
}
}In Action
Once deployed to your desired scope, when creating a Log Analytics Workspace it will deny creation if the Daily Quota has not been set:
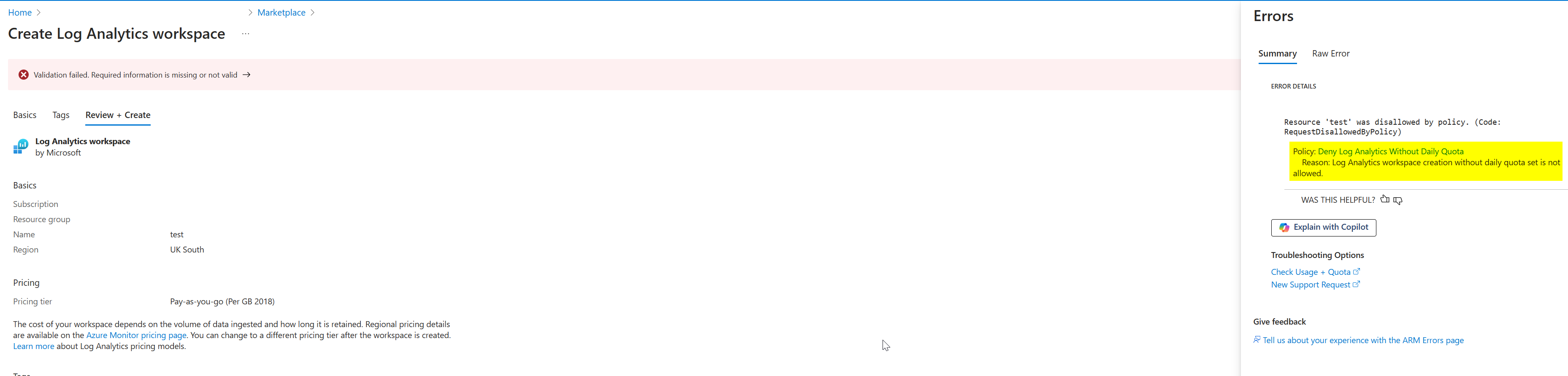
This expands to any deployment method (REST, CLI, Pwsh, Bicep/ARM).
Closing thoughts
A simple and effective FinOps policy guardrail to help ensure engineers across the tenant are deploying workspaces with thought of quotas to guard against potential unexpected log costs. The benefit of this policy that I personally like is that the Portal abstracts away the properties of the workspace, forcing you to create in code, aligning to a modern cloud engineering working practice (of using Bicep for example, and defining a quota there).