Introduction
In this blog I’ll detail how you can create custom resource set definitions (Azure Policy initiatives) from the Azure Monitor Baseline Alerts (AMBA) resources via Enterprise Policy as Code (EPAC). For those unfamiliar with AMBA – it’s a fantastic initiative by Microsoft that provides recommended metrics and monitoring guidelines for your Azure estate – you can deploy patterns (such as Landing Zone) via Bicep or Portal accelerator quickly and easily.
However, when it comes to monitoring resources that are outside of the documented patterns (like APIM, SQL, AI services, etc), and combining this into EPAC there is no quick way out the box to do this. In this blog I’ll go through how you can bolt-on additional resources from the azure monitor baseline alerts services list via EPAC.
You can check out both projects, and their documentation in more detail here:
- Azure/enterprise-azure-policy-as-code: Enterprise-ready Azure Policy-as-Code (PaC) solution (includes Az DevOps pipeline)
- Welcome to AMBA! | Azure Monitor Baseline Alerts
Why include additional resources from AMBA into EPAC?
- Automatically monitor any resources from policy across your Azure estate of your choosing – by using EPAC + AMBA any new resources that get deployed (and old ones too!) you’ll automatically be monitoring
- Policy automatically deploys the alerts with your metrics and can audit if resources have the required alerts deployed
- Build a comprehensive monitoring suite of your Azure estate from the baseline guidelines that AMBA provide
- Allows a GitOps approach to monitoring alerts in Azure
Prerequisites
This blog assumes you have the ALZ pattern for EPAC with AMBA already deployed (so you already have the notification assets for alerting – or at least familiarity on this). If you have not, you can follow George’s guide to get this implemented: Deploy Azure Monitor Baseline Alerts with Enterprise Policy As Code – George Markou. Essentially, you will want to update your EPAC repository with the latest AMBA artifacts from Anthony’s export GitHub (which converts all AMBA ALZ pattern into an EPAC format for you to adopt): amba-export/Definitions at main · anwather/amba-export · GitHub
Creating your definitions in EPAC
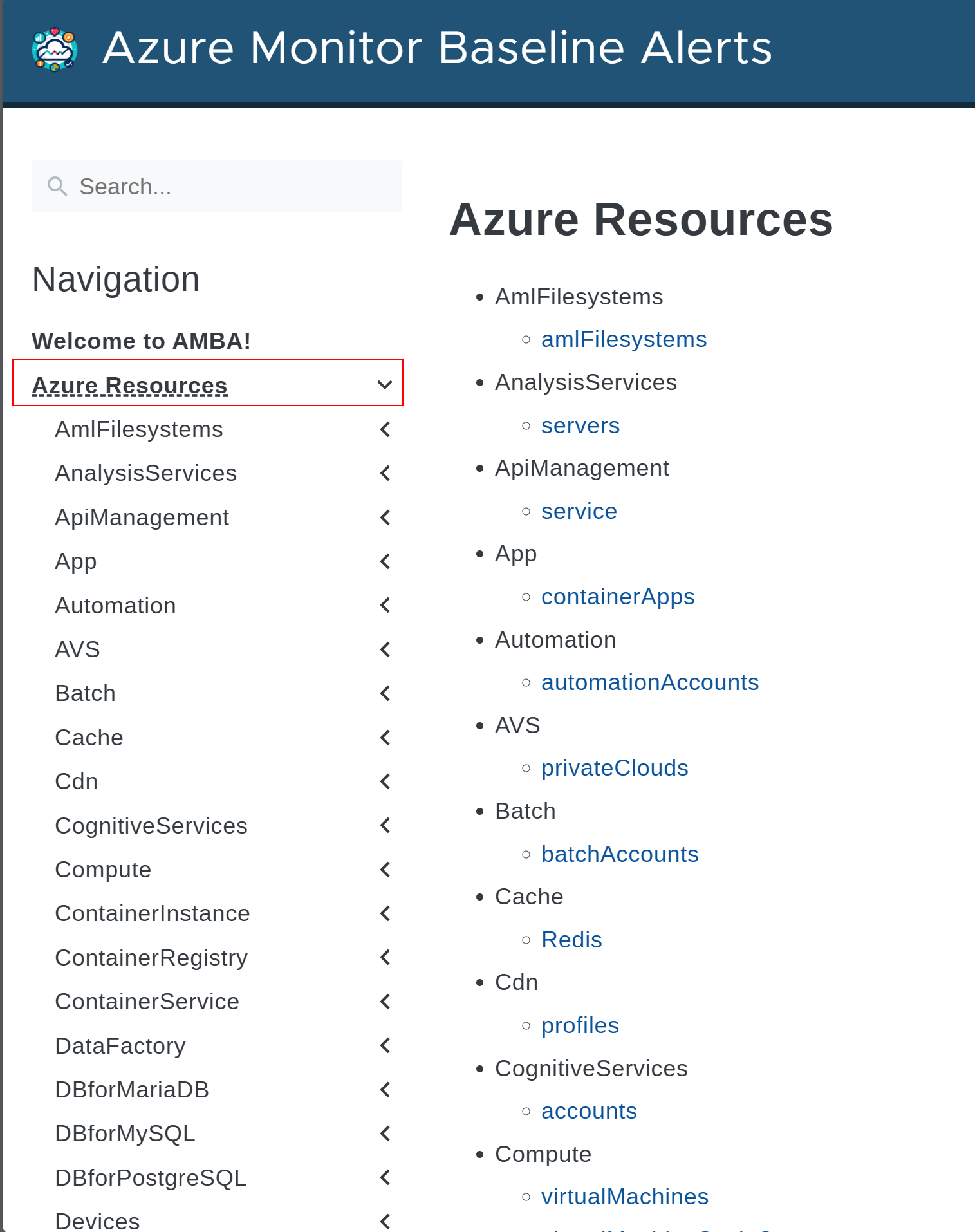
Firstly, you’ll want to select which resource you want to monitor from the services list here: Azure Resources | Azure Monitor Baseline Alerts – it contains many Azure resources that the AMBA team have guideline metric alerts for. In this example I want to monitor the Azure Cognitive Services resource and I want to bundle the alerts of my choosing from this service into a set definition in EPAC to auto-deploy in my Azure estate.
Locate the resource from the list, then go to the first alert you want to create as an EPAC definition:
Select the policy tab on the alert and copy everything from the parameters block to the end of the file:
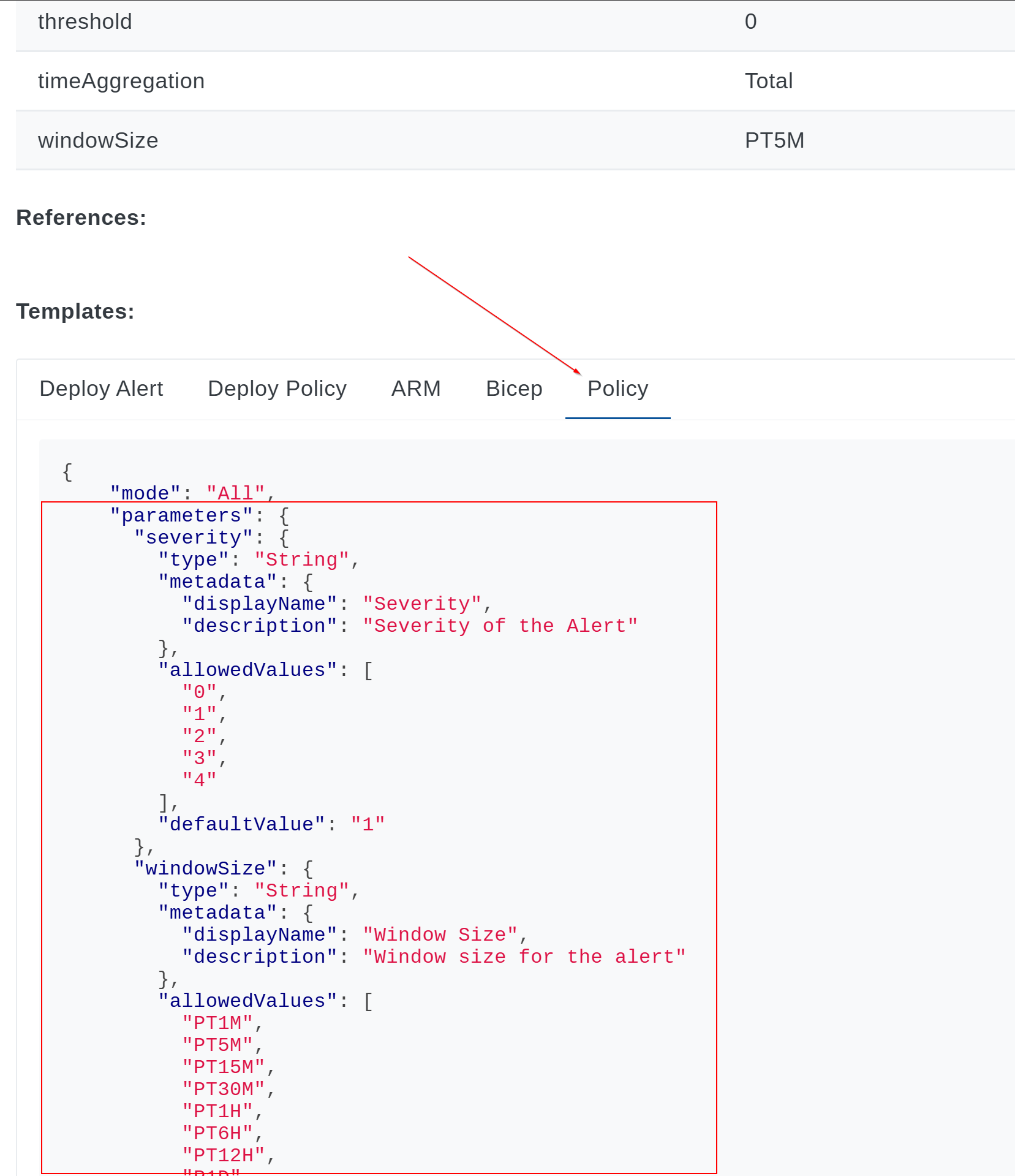
In my example, I’ve selected the Cognitive Services – Client Errors Alert. I’ve copied the parameters block from above and pasted into my deploy_cognitive_client_errors_alerts.jsonc file, as seen below, giving it a unique name, display name, and source from the AMBA URL.
{
"type": "Microsoft.Authorization/policyDefinitions",
"name": "deploy_cognitive_client_errors_alert",
"properties": {
"policyType": "Custom",
"mode": "All",
"displayName": "Deploy Cognitive Client Errors Alert",
"description": "Policy to Audit/Deploy Cognitive Client Errors Alert",
"metadata": {
"version": "1.0.0",
"category": "Cognitive Services",
"source": "https://azure.github.io/azure-monitor-baseline-alerts/services/CognitiveServices/accounts/#clienterrors",
"alzCloudEnvironments": [
"AzureCloud"
],
"_deployed_by_amba": "True"
},
// You can copy and paste this above block for your next definition and tweak the values
"parameters": {
// Paste the Policy parameters from the AMBA policy tab here
...
}You’ll want to repeat this step for each alert you want to use from the resource services on the AMBA page. This is so you end up with a collection of definition alerts that are in EPAC format.
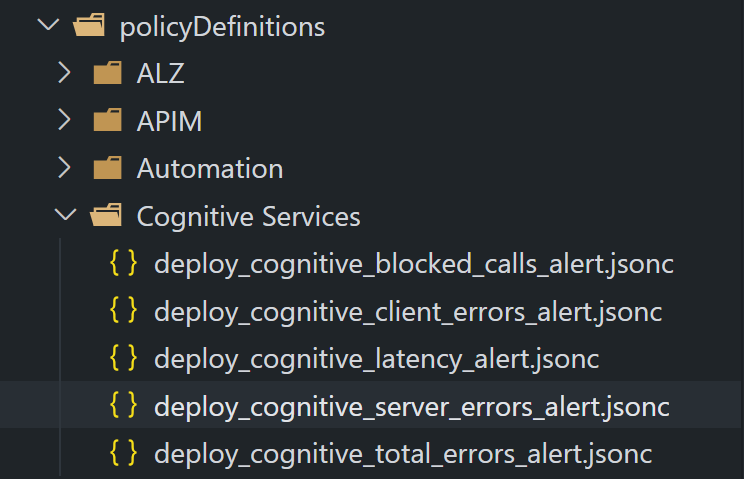
As you can see in the screenshot below, I’ve created 5 alert definitions from the Cognitive Services resource using the method above. Each Policy definition alert is saved within my Definitions/policyDefinitions/Cognitive Services in my EPAC git repository:
Configuring the alert setDefinition
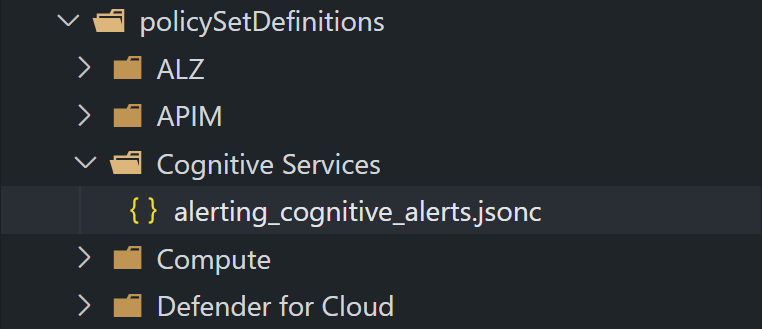
Once you’ve created all the alerts you want – you now need to create a set definition policy so that you can bundle these as an initiative for deployment. Under /Definitions/policySetDefinitions you’ll want to create your initiative, my example I am using alerting_cognitive_alerts.jsonc under an AMBA/Cognitive Service sub-folder:
{
"$schema": "https://raw.githubusercontent.com/Azure/enterprise-azure-policy-as-code/main/Schemas/policy-set-definition-schema.json",
"name": "alerting_cognitive_alerts",
"properties": {
"displayName": "Deploy Azure Baseline Monitor Cognitive Services Alerts",
"policyType": "Custom",
"description": "This initiative deploys the AMBA Cognitive Services Alerts.",
"metadata": {
"category": "Cognitive Services",
"version": "1.0.0",
"source": "https://azure.github.io/azure-monitor-baseline-alerts/services/CognitiveServices/accounts/"
},
"parameters": {
"CognitiveClientErrorsSeverity": {
"type": "String",
"metadata": {
"displayName": "Client Errors Alert Severity",
"description": "Severity of the Client Errors alert."
},
"allowedValues": [
"0",
"1",
"2",
"3",
"4"
],
"defaultValue": "1"
},
"CognitiveClientErrorsWindowSize": {
"type": "String",
"metadata": {
"displayName": "Client Errors Alert Window Size",
"description": "Window size for the Client Errors alert."
},
"allowedValues": [
"PT1M",
"PT5M",
"PT15M",
"PT30M",
"PT1H",
"PT6H",
"PT12H",
"P1D"
],
"defaultValue": "PT5M"
},
"CognitiveClientErrorsEvaluationFrequency": {
"type": "String",
"metadata": {
"displayName": "Client Errors Alert Evaluation Frequency",
"description": "Evaluation frequency for the Client Errors alert."
},
"allowedValues": [
"PT1M",
"PT5M",
"PT15M",
"PT30M",
"PT1H"
],
"defaultValue": "PT1M"
},
"CognitiveClientErrorsThreshold": {
"type": "String",
"metadata": {
"displayName": "Client Errors Alert Threshold",
"description": "Threshold for the Client Errors alert."
},
"defaultValue": "0"
},
"CognitiveClientErrorsEffect": {
"type": "String",
"metadata": {
"displayName": "Client Errors Alert Effect",
"description": "Effect of the Client Errors alert policy."
},
"allowedValues": [
"deployIfNotExists",
"disabled"
],
"defaultValue": "deployIfNotExists"
},
"CognitiveClientErrorsEnabled": {
"type": "String",
"metadata": {
"displayName": "Client Errors Alert Enabled",
"description": "Enable or disable the Client Errors alert."
},
"allowedValues": [
"true",
"false"
],
"defaultValue": "true"
}
"CognitiveServerErrorsEffect": {
// ETC
},
"policyDefinitions": [
{
"policyDefinitionReferenceId": "Cognitive_ClientErrorsAlert",
"policyDefinitionName": "deploy_cognitive_client_errors_alert",
"parameters": {
"MonitorDisableTagValues": {
"value": "[parameters('MonitorDisableTagValues')]"
},
"MonitorDisableTagName": {
"value": "[parameters('MonitorDisableTagName')]"
},
"evaluationFrequency": {
"value": "[parameters('CognitiveClientErrorsEvaluationFrequency')]"
},
"effect": {
"value": "[parameters('CognitiveClientErrorsEffect')]"
},
"windowSize": {
"value": "[parameters('CognitiveClientErrorsWindowSize')]"
},
"severity": {
"value": "[parameters('CognitiveClientErrorsSeverity')]"
},
"enabled": {
"value": "[parameters('CognitiveClientErrorsEnabled')]"
},
"threshold": {
"value": "[parameters('CognitiveClientErrorsThreshold')]"
},
"policyDefinitionReferenceId": "Cognitive_SercerErrorsAlert",
"policyDefinitionName": "deploy_cognitive_server_errors_alert",
"parameters": {
"evaluationFrequency": {
"value": "[parameters('CognitiveClientErrorsEvaluationFrequency')]"
}
// ETC....
}
}
}
]
}
}You’ll want to make sure that each parameter in the setDefinition file is unique to that alert definition, to be able to adjust the values and metrics. For example, CognitiveClientErrorsEffect parameter instead of just effect and so forth. The above example shows just one definition but you would repeat this for each of the definitions you’re including to the initiative.
Configuring the alert policy assignment
Lastly, now that you’ve got your AMBA resource definitions and setDefinitions built you can finally create the policy assignment file. In my case I am using a file called deploy_cognitive_alerts.jsonc within my /Definitions/policyAssignments/AMBA/Cognitive Service EPAC folder structure.
As mentioned in the last step for the initiative, it becomes clear why ensuring each definition in the initiative file needs it’s own unique parameters name so you can set unique parameter values per alert in the assignment. Here’s a simple example below – you’d repeat the below for each alert from the previous step:
{
"$schema": "https://raw.githubusercontent.com/Azure/enterprise-azure-policy-as-code/main/Schemas/policy-assignment-schema.json",
"nodeName": "/root",
"definitionEntry": {
"policySetName": "alerting_cognitive_alerts"
},
"children": [
{
"nodeName": "AI/",
"assignment": {
"name": "Deploy_Cognitive_Alerts",
"displayName": "Deploy Azure Monitor Baseline Cognitive Services Alerts",
"description": "Deploy Azure Monitor Baseline Cognitive Services Alerts"
},
"enforcementMode": "Default",
"parameters": {
"CognitiveClientErrorsSeverity": "1",
"CognitiveClientErrorsWindowSize": "PT5M",
"CognitiveClientErrorsEvaluationFrequency": "PT1M",
"CognitiveClientErrorsThreshold": "0",
"CognitiveClientErrorsEffect": "deployIfNotExists",
"CognitiveClientErrorsEnabled": "true",
"MonitorDisableTagName": "MonitorDisable",
"MonitorDisableTagValues": [
"true",
"Test",
"Dev",
"Sandbox"
]
"CognitiveServerErrorsSeverity": "1",
// ETC....
},
"scope": {
"epac-prod": [
"/providers/Microsoft.Management/managementGroups/mg_landing_zones"
]
}
}
]
}Deploy and remediate!
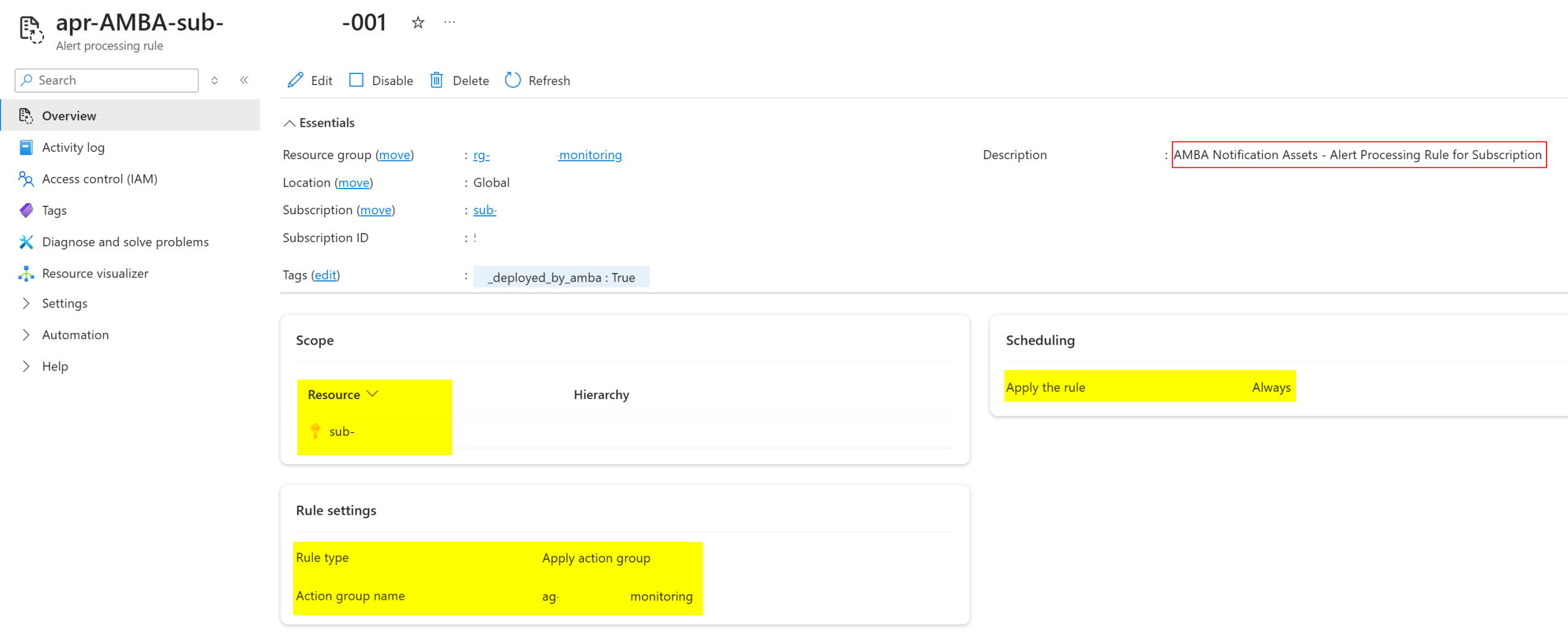
That’s it! After a build, deploy and remediation from EPAC you should now see your newly created AMBA resource service alerts – automatically deploying in your Azure estate keeping your teams proactive on top of issues:
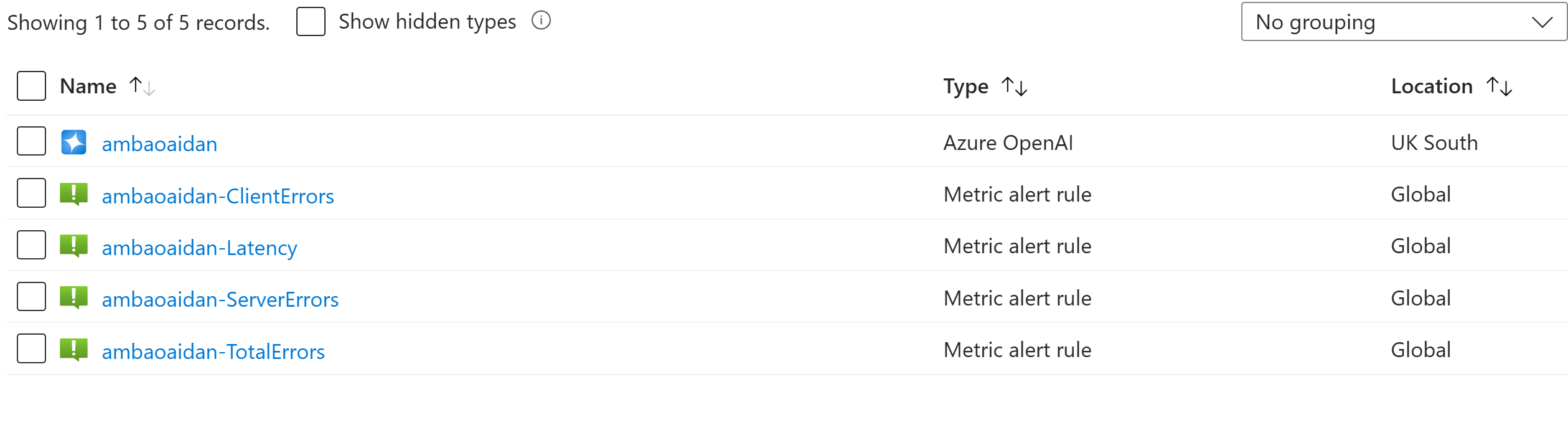
And these additional resource service alerts from AMBA will alert based on your notification-assets ALZ pattern deployment assignment. The alert processing rule 001 is scoped subscriptions, therefore any alert resource you deploy via policy will be caught in this alerting flow ensuring continuity with the rest of the AMBA configurations.