Intro
As you cannot grant owner level permission in Azure Lighthouse (contributor is the highest level available to us) we need to circumvent a way around this limitation for Azure policy remediation.
The solution to this is granting the User Access Administrator role with two delegated roles: Contributor & Log Analytics Contributor. This will allow the managed identity that’s created in the Azure policy to have the correct access in the delegated customer subscription to action the remediation task successfully.
But how do you actually deploy a policy remediation to the subscription via Azure Lighthouse delegation? Microsoft documentation mention this can only be done via the Azure API, aka an ARM template, but doesn’t offer many clear and obviously run-through examples or where to action this yourself. I will detail this in the post below.
AAD Group
Firstly, we need to create an Azure Active Directory security group in our managing tenant that will be dedicated for the policy access. Then we can add this group and the appropriate role(s) into our Azure Lighthouse offering to delegate the correct permissions when deploying a policy in a customer subscription.
Assigning the relevant Azure role(s) in Azure Lighthouse
The role that will be assigned to the security group created will be User Access Administrator.
Additionally, it will then have two delegated role definitions attached to this, Contributor and Log Analytics Contributor.
If deploying your offering via ARM, the section will look like example section below (example Microsoft template for this):
ARM Template Params example
"eligibleAuthorizations": {
"value": [
{
"justInTimeAccessPolicy": {
"multiFactorAuthProvider": "Azure",
"maximumActivationDuration": "PT8H"
},
"principalId": "00000000-0000-0000-0000-000000000000",
"principalIdDisplayName": "lighthouse-az-policy",
"roleDefinitionId": "18d7d88d-d35e-4fb5-a5c3-7773c20a72d9",
"delegatedRoleDefinitionIds": [
"b24988ac-6180-42a0-ab88-20f7382dd24c",
"92aaf0da-9dab-42b6-94a3-d43ce8d16293"
]
}Managed Services Marketplace Offering
Alternatively, if deploying an Azure Marketplace offering for managed services, your technical configuration manifest will need an additional authorisation added to it. For example:
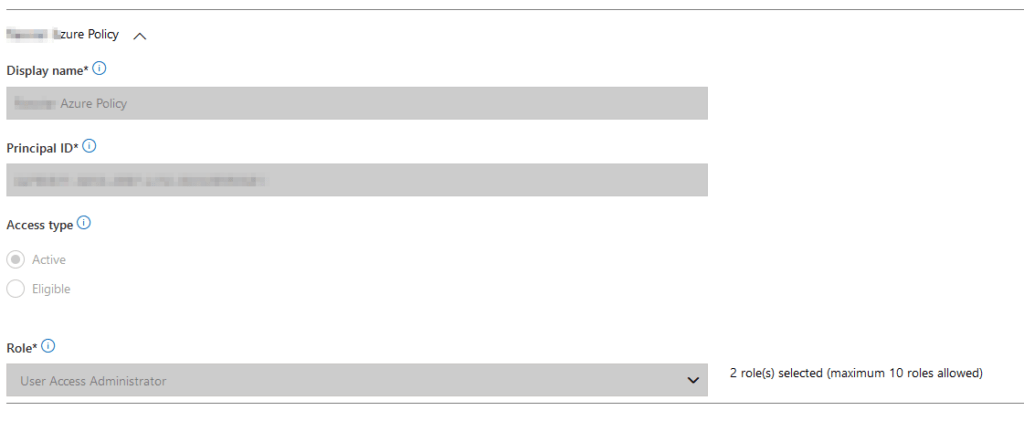
Display name: Rios Azure Policy
Principal ID: ID of AAD Security group
Access type: Active
Role: User Access Administrator
Delegated role(s): Contributor, Log Analytics Contributor
Deploying policy remediation into delegated subscriptions through Lighthouse with PIM
We cannot deploy Azure policy remediation tasks via the Azure Portal for delegated subscriptions from Azure Lighthouse.
Therefore, you have to deploy policies via ARM templates in order for remediation permissions to be created successfully when the managed identity is created.
Note: the ARM deployment is done from the managing tenant, not your customers tenant. Specify the customers delegated subscription during deployment.
Prerequisites
- Be a member of the lighthouse security group which has contributor access to the customer tenant
- Be a member of the new lighthouse security group which has the user access administrator as per above
- AzCli PS module
Assuming the delegated subscription is now running your latest lighthouse offering with the new security group permissions, we can now proceed with deploying a policy (make sure you’re a member of that group!).
An example tags ARM policy template is located here.
Deploy this from your managing tenant, specify a random GUID for the rbac guid parameters. In my example I am deploying via AzCli, for example:
$ az login
$ az account set --subscription "Customer Subscription Display Name"
$ az deployment sub create --location "uksouth" --template-file "C:\ARM\Policy.json"Then once deployment is completed, you should be able to locate the policy in customers subscription > Policies > Edit assignment > Remediation and this will confirm the policy has the correct remediation ‘contributor’ permission under the managed identity object. (if it is blank, something is not setup right check my troubleshooting tips).
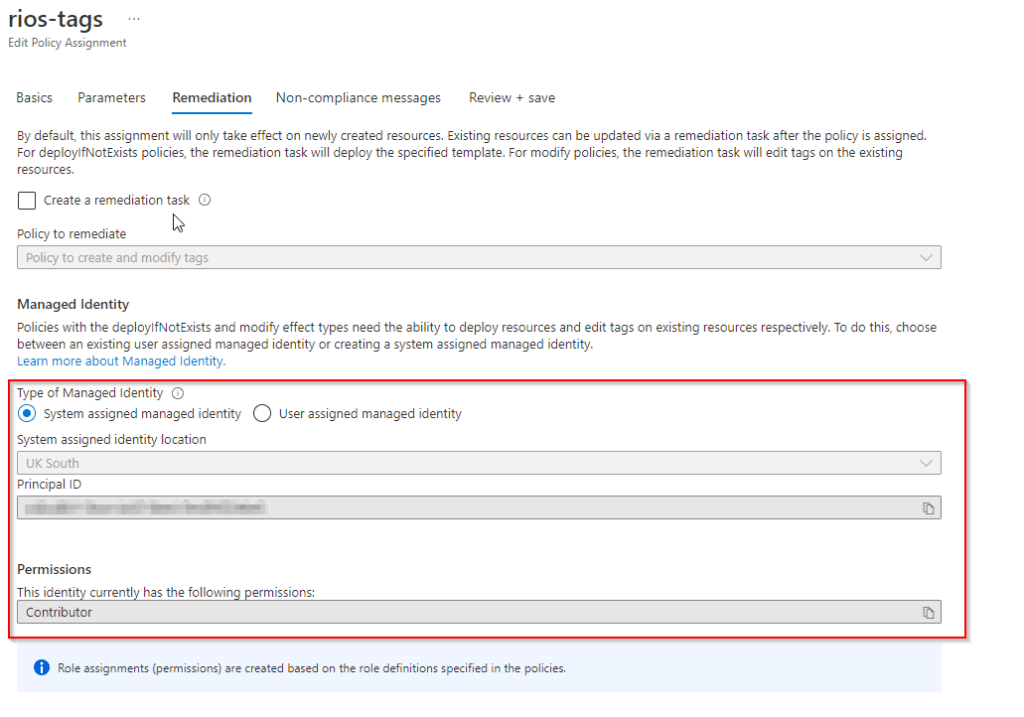
Now you’re able to create remediation tasks in the customers delegated subscription successfully!
Troubleshooting
You specifically need contributor role to be activate in PIM for that subscription to be able to deploy a policy or you won’t be able to deploy the policy at all.
You’ll need to be a member of the new lighthouse security group in order for the remediation permissions to be successful.
Check the customer has the latest up to date offering of your Azure Lighthouse for this to work.
If you do this via the Azure Portal it will allow you to create a policy successfully, but the remediation permissions won’t be correct, and it will fail a remediation task.
Helpful URLs:
Lighthouse Template samples https://github.com/Azure/Azure-Lighthouse-samples
Creating a marketplace offering https://docs.microsoft.com/en-us/azure/marketplace/create-managed-service-offer
Publishing a marketplace offering https://docs.microsoft.com/en-us/azure/lighthouse/how-to/publish-managed-services-offers
Creating eligible authorisations for PIM https://docs.microsoft.com/en-us/azure/lighthouse/how-to/create-eligible-authorizations
https://learn.microsoft.com/en-us/azure/lighthouse/how-to/deploy-policy-remediation deploy policy remediation
2 thoughts on “Deploying Azure Policy remediation via Azure Lighthouse with PIM”