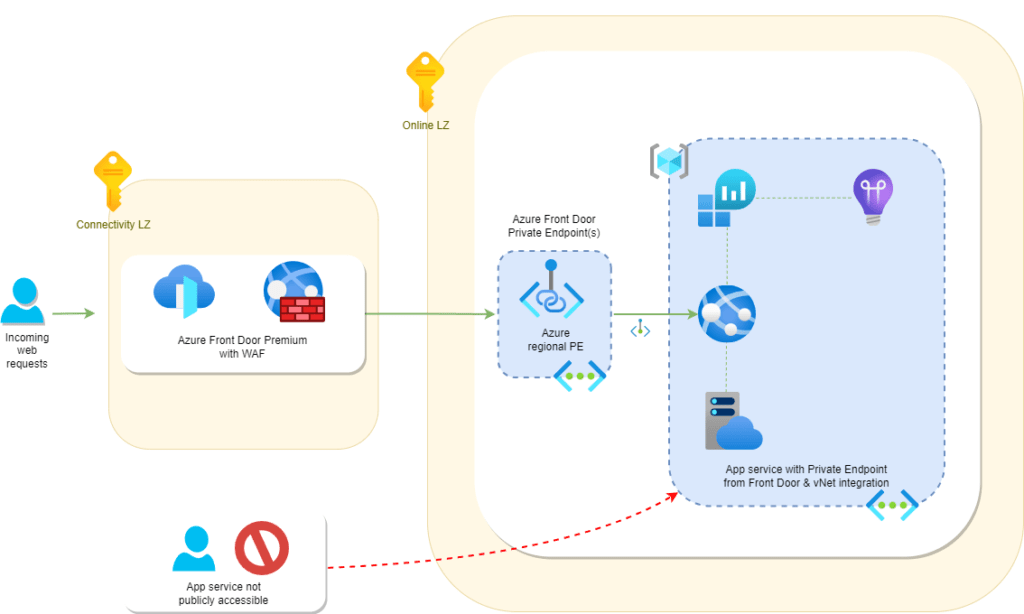
Introduction
Azure Front Door Premium allows Private Link connections to Azure PaaS services such as Azure Storage, App services and even AKS/Azure Container Apps.
Private Endpoints allow us to securely send traffic via the Azure backbone network with Microsoft directly to your virtual network without leaving and going via the internet.
In this post I’ll detail the benefits of Azure Front Door Premium integration to your Azure App service, what the deployment looks like and an Azure Bicep template to quick start deploy all the components in a matter of minutes!
Benefits
Seamless integration. Front Door will directly connect to the origin backend directly rather than having to transverse through public service endpoints.
Security. Using a Private Endpoints means the traffic is not sent out to the web and is retained within the Microsoft backbone to your private internal virtual network.
Only one Private Endpoint needed. Microsoft handles this and you only need to approve the PE once to your backend origin and it’s all done!
Considerations
- Regions available for Azure Front Door Premium with Private Link are lacking – UK West is missing at the time of writing for example.
- Private Endpoints add additional costs and complexity that may be not necessary for your end goal or business needs.
- Can alternatively setup an AzureFrontDoor.Backend Service Tag on the Azure Web App access restrictions, specifying your Front Door GUID to lock it down.
Deploying Azure Front Door Premium with Private Endpoint to App Service backend
The components deployed & automatically configured by the Bicep template are as follows:
- Azure Front Door Premium with WAF
- Private Link to App Service (pending status)
- Windows App Service & App Plan
- Log Analytics workspace
- Enabling App Insights
- Enabling system-assigned managed identity on the app
- Virtual Network & vNet integration
All of the Azure Bicep code used is uploaded to my GitHub here.
Fork the repository and deploy using the instructions in the README file after amending the parameters to suit your deployment needs.
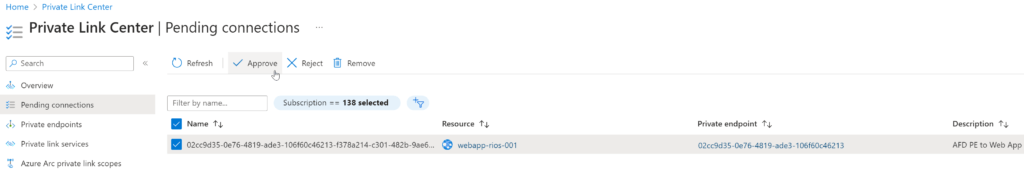
Once deployed, in the portal search bar, locate Private Link Centre and under the Pending connections approve the connection:
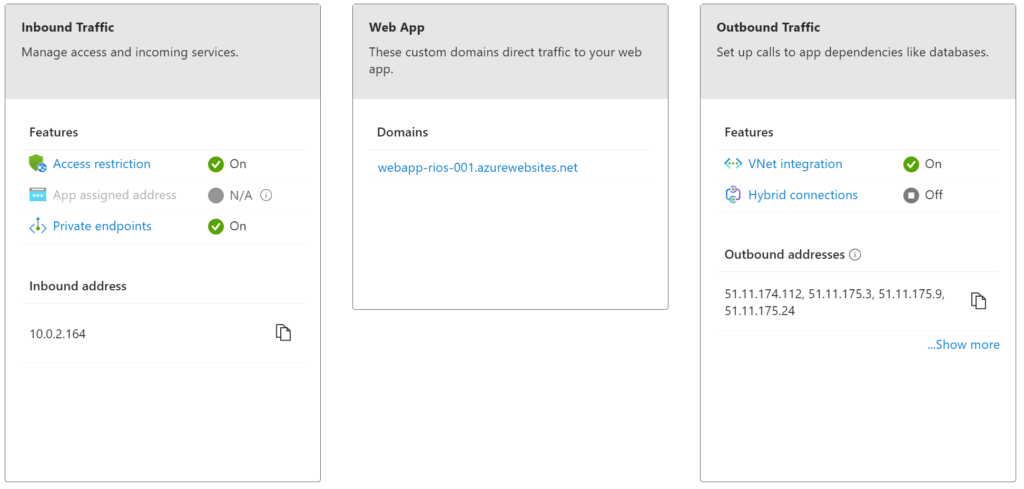
In the newly created Azure App – Networking tab we can now see that the Private Endpoint is configured, along with vNet integration and public access denied via Bicep.
Then, checking the Azure Front Door Origin group we can see Bicep has automatically populated the private link service and it’s details:
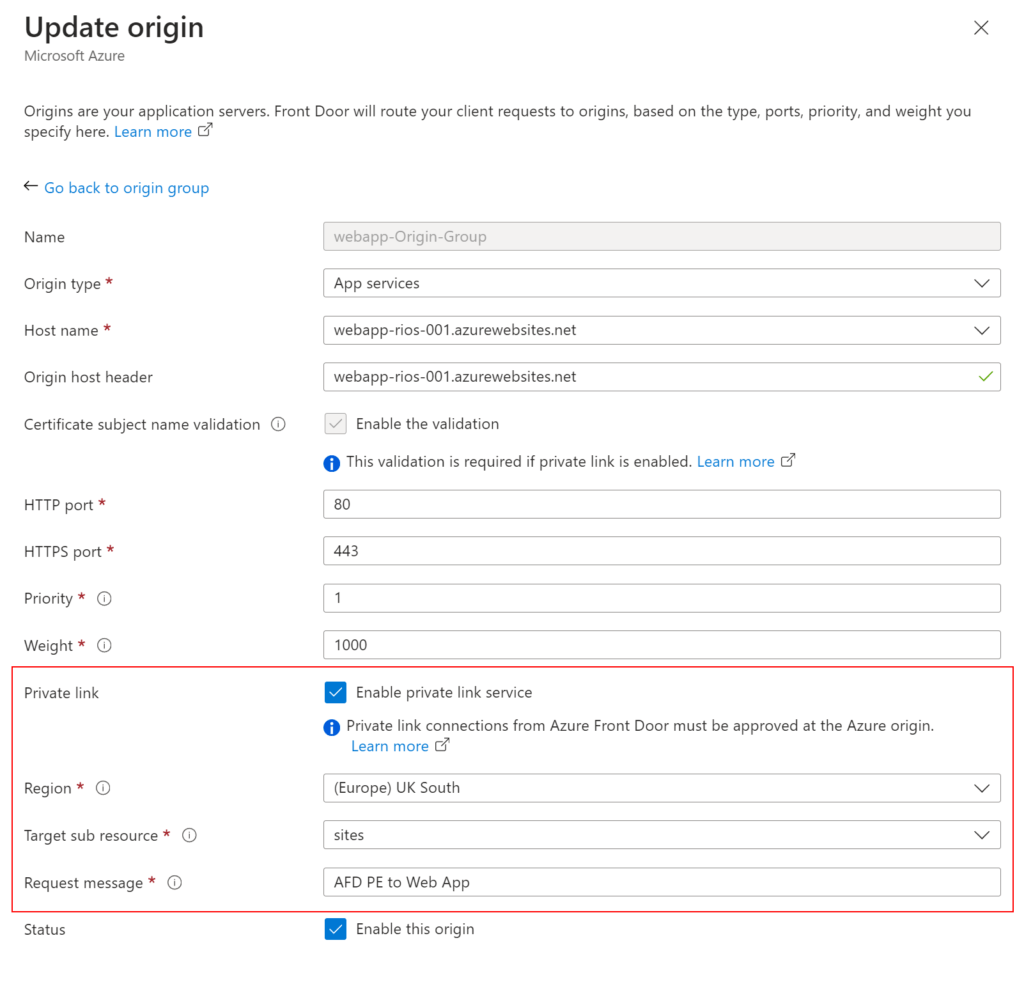
Here, we can see the Bicep template has automatically enabled the Private Link service on the origin and specified the region, sub resource of sites which refers to the underlying Web App ‘serverfarm’ resources and a simple message for the Private Endpoint requesting message.
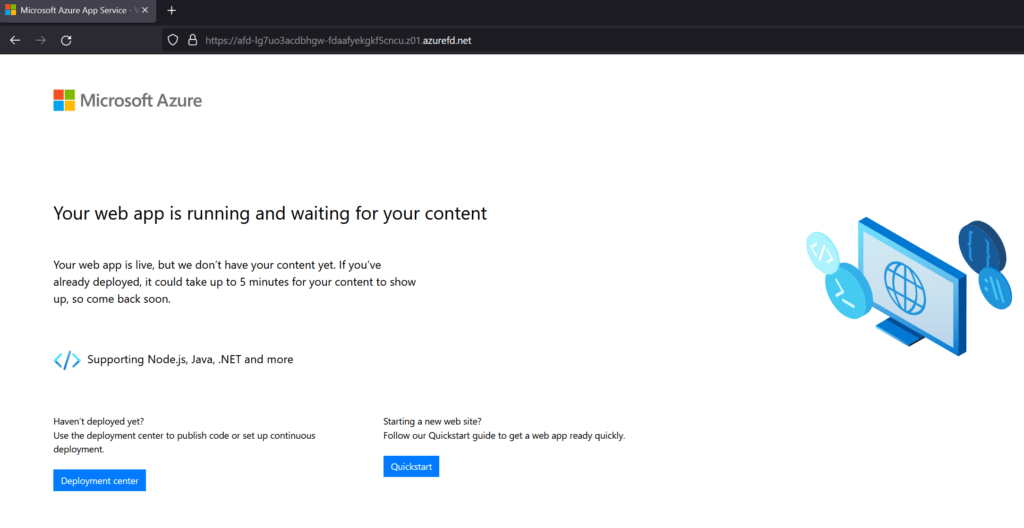
Lastly, checking the Front Door endpoint URL we are able to resolve directly to the default web app splash page to confirm it’s all working:
Conclusion
That’s it! Really sleek and elegant solution to securing your PaaS services behind Azure Front Door Premium features. You can easily amend my Bicep template to change the app SKUs, or code stack etc.
I’ve further tested this setup with Azure Container Apps and it works flawlessly too. You just need to use the Microsoft managed Kubernetes load balancer as the origin host for it to work.
The initial Bicep code is from the Bicep ResourceModules repository over on GitHub (aka CARML aka soon to be Azure Verified Modules), and modified for this deployment.
There is an example of Front Door Premium with App Services Bicep on Microsoft Learn, however, it does not enable Private Link & does not turn on any features such as Application Insights, managed identities, vNet integration, etc.
This is partially what spurred me on to create this more conclusive quickstart template and guide to compliment.
References
Pricing – Front Door | Microsoft Azure
Comparison between Azure Front Door and Azure CDN services | Microsoft Learn
Secure traffic to origins – Azure Front Door | Microsoft Learn