In this guide I will cover how to utilise the Azure REST API to invoke RBAC assignment to Azure Resoure Groups from a Logic App or Power Automate HTTP connector.
This can be useful in business logic to automate assignments where they need to be specific to certain resource groups rather than inherited from the subscription to every resource group.
HTTP Connector
Firstly, search and add the HTTP action into your flow.
Method & URI
Secondly, select the PUT method from the drop down.
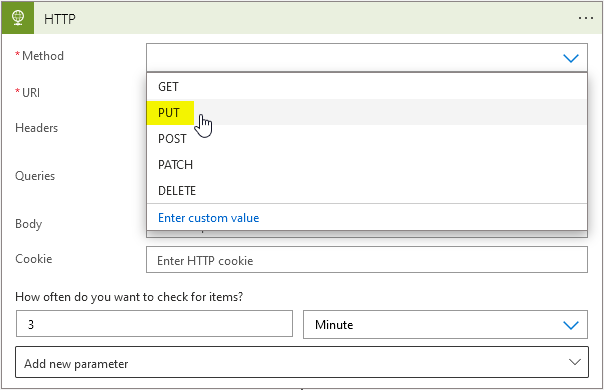
Next lets compile the URI for the request – I’m using a randomly generated GUID for the role assignments so it is unique for the request.
https://management.azure.com/subscriptions/YOUR-SUBSCRIPTION-ID/resourceGroups/YOUR-RG-NAME/providers/Microsoft.Authorization/roleAssignments/()guid?api-version=2015-07-0For the randomised GUID I would strongly recommend using an expression to generate a new string every run. You can use guid() as an expression to achieve this.
Request Body
Next lets locate the AAD group object ID which will be required for the request body. Search for Active Direcotry in Azure and navigate to Groups, search the group name and copy the Object Id.
Afterwards we’ll need to compile the request body and paste into the connector:
{
"properties": {
"roleDefinitionId": "/subscriptions/YOUR-SUBSCRIPTION-ID/resourceGroups/YOUR-RG-NAME/providers/Microsoft.Authorization/roleDefinitions/RBAC-GUID",
"principalId": "AD-OBJECT-GUID"
}
}To locate your desired RBAC guid in the request body, go to a resource group and select Access Control on the left navigation pane. Next, select the desired role and go to the JSON tab. The GUID for the roles can be found in the example:
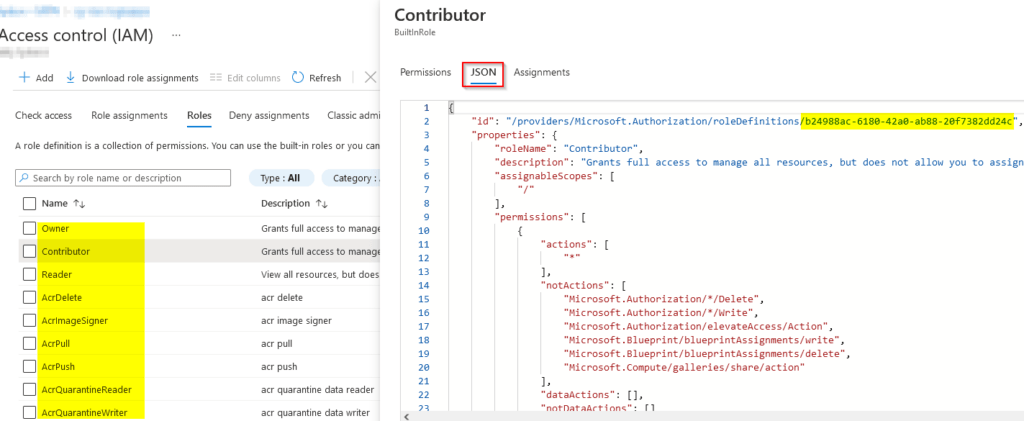
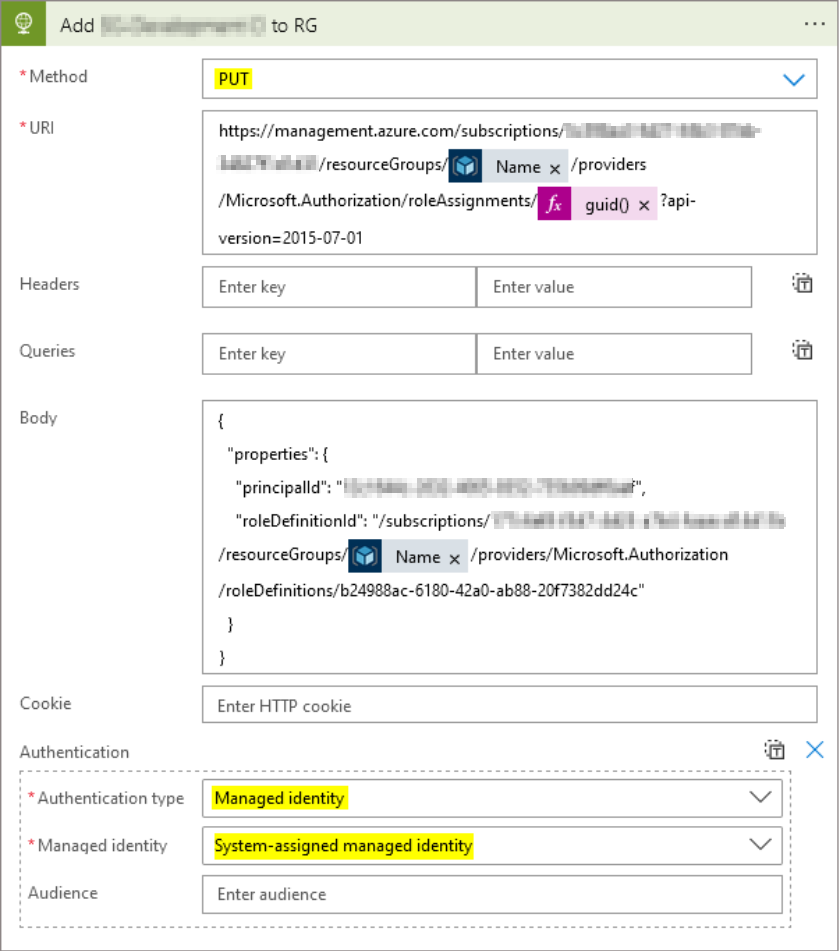
In my example I will be using the Contributor access role and I’ve used the Resource Group name from a previous action in my flow. Here’s how the full connector request is looking like:
Managed Identity
This is a perfect example of where managed identities can be a great use case. Importantly this is because it’s removing the over head of managing service accounts in addition to providing additional security.
Firstly, turn on the system managed identity in the Logic App. Before proceeding further it may be best to allow for any sync delay before testing.
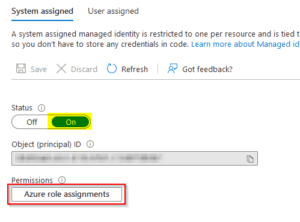
Afterward assign an RBAC role for the identity permission. In my instance it was owner on the subscription level.
Lastly, go back to the HTTP connector and select the drop down menu ‘Add new parameter’. Then select managed identity to use it as the REST API authentication method in the request.
Output
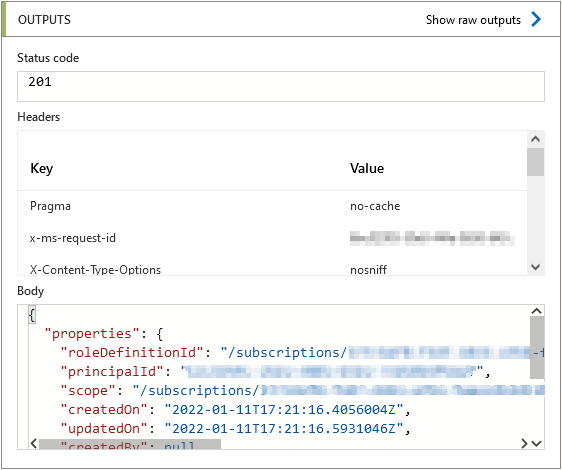
Finally lets trigger the logic app manually to see if the request is accepted successfully.
As you can see in my example, I get a ‘201 status’ response in my output showing that the request was successfully accepted by the Azure API.
When checking the resource group IAM I now see the AD group listed as a contributor role.
Over to you 🙂
Summary
I’ve been utilising the above API invoke after Azure Resource Group creation so I can automatically assign RBAC roles within the Logic App flow. Alternatively you can changed the principal id to an individual user using the same method if required.
This is a great way to harness managed identities in flows coupled the Azure REST API to automate IAM in a business flow or IT process
References:
https://docs.microsoft.com/en-us/rest/api/authorization/role-assignments/create https://docs.microsoft.com/en-us/rest/api/authorization/
Troubleshooting tips
Allow some time for the managed identity permissions to go through.
Make sure to use a supported client API version.
Using Visual Studio Code to verify JSON syntax was helpful for the request body. The API can be sensitive to syntax and can sometimes return misleading errors.
{
"error": {
"code": "RoleAssignmentUpdateNotPermitted",
"message": "Tenant ID, application ID, principal ID, and scope are not allowed to be updated."
}
}When receving the above error output, review your GUID in the URI body – this must be unique otherwise you will get the above error. Try a new GUID and this should resolve the issue. As I mentioned earlier in the guide using an expression guid() is an easy way to do this.
Nice! Used this in an AVD deployment to give users a way to temporarily gain admin rights on personal hosts 🙂
That sounds like a really cool use case, nice one Jos!